Deep, Dark web
An ocean of data
Yes. You can see the internet as an ocean. When you think of the ocean it comes to your mind, most certainly, two very different pictures of it. One above, another bellow the ocean surface. Much like the case of an Iceberg, you know that much more has to be seen bellow the surface than that above. Well, the same happens with internet data. On the internet the ocean surface is the data that is indexable by the search engines. Some also call it the visible web. This is because people mainly use search engines to search for new data. If some data is availabe on the internet but is not indexable by a search engine we say that this belongs to the deep web.
Yeah sure, but what about the dark web?
Dark web is not indexable by search engines so it is certainly a part of the deep web. The term is not particularly clear but we can say that these are contents that are available on the internet in the form of an overlay network. Virtual Private Networks (VPNs) are a particular case of a overlay network which, also, is not indexable by search engines. Most certainly it should be considered part of the dark web, but it isn't. The same happens for contents presented in mail servers, private cloud providers and so on. So the definition it seems to be a little bit wrong. From what we see in popular culture. The best definition found was
The part of the World Wide Web that is only accessible by means of special software, allowing users and website operators to remain anonymous or untraceable.
This seems more accurate. With this definition it is easy to see why mail server contents, vpn networks and data based in private cloud service providers don't belong to the dark web.
Tor and the Onion Services
One particular case of service that definetly belongs to the dark net is all the content served in The Onion Router. The Onion Router is a routing system of the best onions on the planet? Well, not exactly. But yes it is a routing system. The Onion Router has its name derived from the way it routes the traffic, onion routing
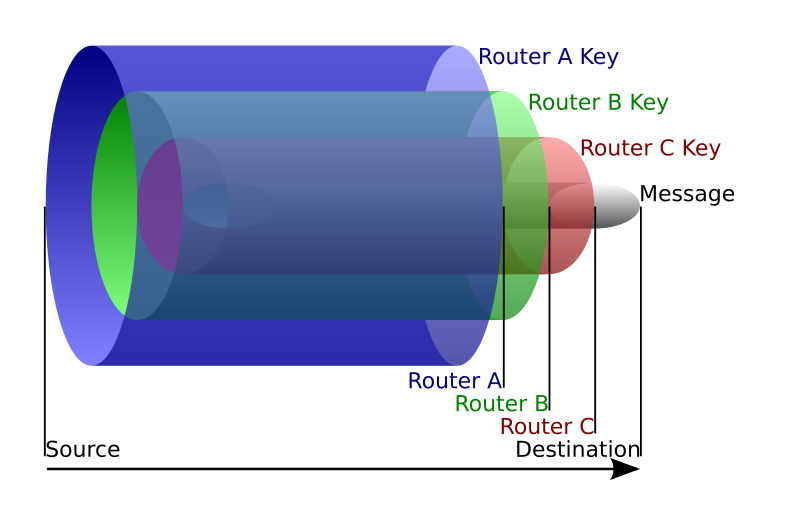
The above picture is a good visual explanation for what is happening when your surf the web through the TOR system. Your traffic is encripted and sent into a total of three hoops from a pool of available peers.
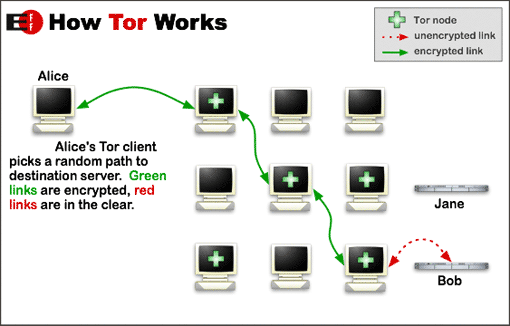
The traffic is encrypted beetween all the nodes to provide secrecy. By avoiding direct connections between nodes and services it adds another feature some degree of anonimity. Note, however, that the traffic between the last tor node and the end service may be not encrypted and so can leak confidential and compromisable information. The nodes in the tor network that forwards the messages are called relays and the last, the one that does the last jump, is called exit relay. In the picture above the node that communicate directly to Bob is the exit relay.
Tor and VPN
Virtual Private Networks are a particular case of overlay network that sits on top of an underlying network, usually internet. Since tor is a web based application used to route http/https services it is possible that other applications running in your pc leak important information that enable eavesdropping through data correlation. To add a higher level of anonymity it is usual to see a combination of tor and vpn services.
Onion Services
Initially Tor was developed to achieve privacy and anonymity on web browsing with the use of an onion routing system. This had been of great help for many human beings that were behind the censorship of many, not so open, countries. However the onion routing only solves one side of the censorship. While many people found a way to connect to censored data they were not able to publish their own information. Imagine Bob in North Corea. With onion routing Bob was able to read the Le Monde in France. Bob was not able, however, to build his own version of Le North Corea web site. Why? Services on the web follow the traditional domain approach. For this he would need to register a domain and host his own website with the newspaper data. To block the access and identify the person responsible for the site is a trivial job. By following this road Bob would end, quickly, in one small cell in a cold place in North Corea.
It was needed a reverse onion routing system
To achive bi directional anti censorship mechanism the tor project devise a scheme called onion services. The idea is an extension to the onion routing already implmented, a rendevouz point and a service discovery mechanism.

The service discovery, responsible to resolve an identifier into a host, is implemented as a distributed hash table a descentralized data structure. With a descentralized approach tor difficults the mission of censorship agents.
But wait! If the service discovery resolves to Bob he is in a nasty situation.
Thats true. Hence a rendevouz endpoint. Rendevouz endpoints are nodes that will bridge the contents provided by Bob. While these onion hidden services are not bulletproof they offer a pretty good way of censorship circunvention.
All very interesting. But what has all this has to do with dark net or deep web?
Fair enough. First note that onion services run on the onion routing framework. Since TOR is an overlay network in the internet the content available as a onion service is not indexable by web search engines since these target primary content available in the primary network, the internet.
But there is more. By looking to the main goal of tor arquitecture we also must conclude that onion services belong to the dark net since tor adds a fair amount of secrecy and anonymity.
Yes this is all very interesting but what are we really talking about here? Where can I find and use these dark sites?
Since they run on the tor overlay network you will not find them with your tradicional browser and google queries. First you must download tor browser. This is a mozilla firefox based browser that was addapted to route your traffic through the onion.
But yeah. What now? Now you must search for .onion endpoints. These are not readily available from traditional search engines. However after some digging you'll find specialized onion search engines like the TORCH or Ahmia.
Underworld Services
After spending some hours these are some of the hidden services found
- Dream Market - Drug selling site
- Tor Shops - Aggregator of other shops
- Kamagra - Viagra black market
- UK Guns and Ammo Store - Guns and ammo UK based shop
- Counterfeit USD - Counterfeit USD shop
- Mobile Store - Smartphone black market
- Torminator - Hitman market
These are some of many, many more hidden services available. Unfortunately these are bad examples that give bad reputation to the network. The problem with this type of services is that they give bad reputation to a good tool. In the future if the gross majority of tor traffic is used for criminal activities those who need this tool the most will mostly suffer from increase censorship from states.
The idea with this post was to serve as an introduction to a not so mainstream set of tools the cons and pros and ultimately the future of private privacy as we know it.